- Home
- Our Approach
This is one of the first questions we ask you when we initially meet. It’s really the only way to know if we’re the right ones to support you and your business. Plain and simple – you talk, we listen. This allows us to develop the right service solution for your unique needs. Your answers allow us to provide insight into how your security can also grow with your business. It’s this conversation where, together, we can:
-
Remove uncertainty and build confidence in scalable and repeatable solutions.
-
Discover where you need predictability in the unpredictable world of cybersecurity.
-
Gain deeper clarity of your real vulnerabilities to deliver real solutions.
-
Connect the risk gaps between business sustainability and cybersecurity architecture.
-
Create action to take the right next steps for your path forward.
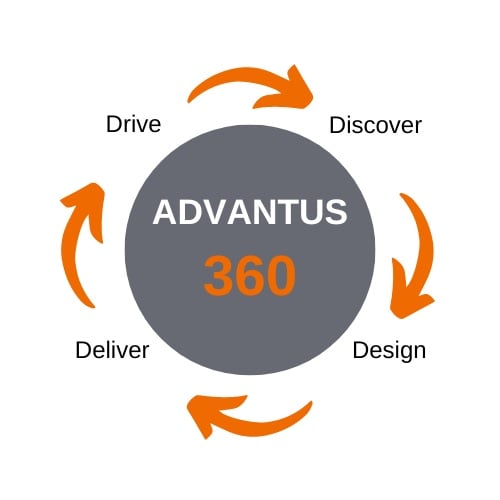
The ADVANTUS360 Approach
Of course, we do have a framework for our approach when designing your customized solution, which we’ve broken down into four key areas:
Discover, Design, Deliver, Drive Forward
This is the beginning of our journey - the question-and-answer portion to gain full clarity. Here, we assess your primary needs for risk reduction, incident preparation and response development, operational efficiencies, and business enablement. This is how the breadth and type of technical expertise, software, and processes required are identified. Areas often uncovered for security development involve:
- Solutions that enhance your current business and IT infrastructure.
- A high-level security structure that protects you and your customers.
- A user-focused approach and training for easy implementation of the new system.
This is what we consider flexible and responsive engagement that adapts solutions based on your project and overall operational needs.
Design
Once discovery is complete, we begin designing your solution. This can be as simple as providing access to a product from one of our vetted partners or an in-depth top-to-bottom design and management of a custom solution. This solution becomes the road map for security implementation and execution.
Within the design, we ensure our collaboration to bridge gaps in skill sets to achieve the objectives of your specific project. Within our designs, we often include a focus on:
- Protecting your business brand and reputation.
- Ensuring we are a genuine fit with skills and personality.
- Managing threats before they happen.
- Disrupting any attacks to avoid information loss.
- How to adapt with a quick response as needed.
Armed with the right solution and roadmap for implementation, we deliver on promised solutions. Whether we’re completing the entirety of the project, or seamlessly integrating into your own team, what remains consistent is the delivery of quality execution, service excellence, and dedication to building our relationship.
Throughout our service delivery, we hold ourselves to providing an exceptional experience. One where we properly connect your people to the technology for a deeper understanding of how your business is secured online.
The completion of a project is just the beginning. The cybersecurity industry is in its infancy, and you need a reliable partner committed to evolving with the technology. Here, we strive to add long-term value through the delivered solution by ensuring it remains valid as technology evolves. There is no finish line when it comes to security, and you deserve a dedicated team committed to ongoing cybersecurity adaptation and readiness. This is how we can support you to drive your organization’s vision forward in the ever-changing technology industry.
Through our approach, we successfully leverage industry best practices, platforms, and solutions to achieve cybersecurity effectiveness as the technology – and your business – evolves.

SECURE
Alan Brazendale, Director, Technology Enablement
ADVANTUS360 always makes me feel like we’re their number one priority. It’s in the coffee conversations we have, the quarterly updates that allow us to reaffirm we are going in the right direction, the insights and resources they provide without any sales expectation, and how they always pick up the phone. They are always there. We have always gotten value out of any project we’ve moved forward with and trust that they will cover our backs, allowing us to put our best foot forward. Transparent, communicative, insightful, and enjoyable to work with, ADVANTUS360 is a true partner who always has our best interests in mind.

SIGA
Geoff Cole, Director of IT Infrastructure Services
ADVANTUS360 is a true IT security partner. Regan brings a unique ability to see beyond the immediate solution required. He gives us the ability to pivot in the future, with the ability to scale should we need to. Because of the work that ADVANTUS360 has done, guided by Regan’s understanding of where we are today and the possibilities of where we’re going, we have more visibility on what’s going on in our network via the optimized systems and solutions developed. With ADVANTUS360, we’ve been able to reduce incidents and response times within our network through the greater 360 view of their approach. This is a company who will walk with you through the good, the bad, and the ugly within the security landscape. There’s a dedication to service, conversation, and evolution throughout every phase of a project, including the ongoing maintenance phase. Most importantly, Regan brings a deeper understanding of the human element required within security, which helps us to implement solutions that connect our people, capabilities, and greater business objectives. Without a doubt, I would recommend ADVANTUS360 to companies looking for a partnership.

Rogers Insurance Ltd. - Acera Insurance Services Ltd.
Lloyd Freiday, Vice President, Information Technology
What first started with a need to quickly solve a network outage emergency has turned into a long-term relationship since 2015. Over the past seven years, ADVANTUS360 has become our trusted cybersecurity strategic partner, providing consulting services and resources that solve the problems we’re actually having while setting a clear direction for how to move forward and improve as an organization. They have a clear passion for the industry, are willing and able to provide valuable advice, and can move projects along quickly because of the collaborative culture they’ve developed. I value the individual relationships we’ve built over time, finding consistency in who and how we work together. Honest and forthcoming, anyone responsible for IT security would find them a great partner to have because of their knowledge, flexibility, and desire to add value for future growth as technology continues to evolve.

Bankers Petroleum Ltd.
Connect with us today to uncover how our cybersecurity approach can work for you.

